Author: Elma Dilaver Gheith
Viewers: 2,951
Last month viewers: 63
Categories: PHP Tutorials, PHP Security, Sponsored
Fortunately it is possible to detect when users are behind proxies by looking up their IP address using IP2Proxy databases of known proxies.
Read this article to learn how to use IP2Proxy database to detect when users are behind proxies, so you can take the necessary measures to avoid that those users may cause some kind of harm.
Contents
Introduction
Types of Proxies
Proxy Types Anonymity Level
Malicious Uses of Proxies and Prevention
IP2Proxy
Basic Structure of IP2Proxy in the CSV format
How to Import the Database into MySQL
How to Query the Database in MySQL
IP2Proxy Web Service
Conclusion
Introduction
A proxy is a server which acts as a means of communication between the client and the server. It offers various advantages while accepting the incoming requests from the client before sending them to the server.
This way, the incoming traffic can be filtered and controlled. That is why a proxy can protect the user privacy as well.
A proxy is very useful for different kind of companies, as well schools and even for governments. But proxies are often used from individuals, because besides protection, it also provides anonymity to a certain level.
With a proxy server, incoming traffic can be monitored, which makes the censoring of undesirable content much easier.
Types of Proxies
Users can choose between different kinds of proxy servers, depending on their needs. The access to some proxy servers is often a commercial service, but there are also great proxy servers out there which are free.
TOR Network
Proxy servers from the Tor (The Onion Router) network are available for free and enable online anonymity by encrypting and re-encrypting the original data multiple times by using a technique called onion routing. This way, internet traffic becomes more difficult to trace and users' privacy, personal freedom and personal communications are being protected.
I2P Network
Another type of free proxy server is the I2P anonymous proxy, a proxy network which also provides a high level of anonymity. I2P uses the technique called garlic routing, which represents an enhancement of the onion routing. Its goals are also protecting the privacy and personal freedom of users, but also the ability to conduct confidential business.
Web Proxy
Web proxies are capable of providing the user access to sites, which are blocked by other proxies, like those of schools or corporations. Using a Web form, the user can request a target URL in his own browser, where he also gets the result of the request. This proxy also hides users' IP address that is why it also provides certain level of anonymity.
VPN: Virtual Private Networks
Another way to provide secure connection between different users, like in case of employees in companies, is the usage of Virtual Private Networks (VPN). Those proxies are a result of an extension of the private network across a public network. VPNs are also being used from individuals to secure their wireless transactions, as well to connect to proxy servers.
Data Center and Hosting Providers
Individuals and companies often use the services of hosting providers or data centers (DCH) to host their own proxy servers. This way they can connect to the public Internet via their own servers.
Public Proxies
The easiest way to gain anonymity while being on the web provide public proxies. Users just need to know the proxy IP address and its port and connect it using without any restriction. It is usually free and thus it is very popular and common.
Proxy Types Anonymity Level
All proxy types provide different anonymity levels. A high anonymity proxy provides better protection in terms of protecting users personal information such as their real IP address.
| Proxy Type | Description | Anonymity |
|---|---|---|
| VPN | Anonymizing VPN services. These services offer users a publicly accessible VPN for the purpose of hiding their IP address. | High |
| TOR | Tor Exit Nodes. The Tor Project is an open network used by those who wish to maintain anonymity. | High |
| DCH | Hosting Providers/Data Center. Since hosting providers and data centers can serve to provide anonymity, the Anonymous IP database flags IP addresses associated with them. | Low |
| PUB | Public Proxies. These are services which make connection requests on a user's behalf. Proxy server software can be configured by the administrator to listen on some specified port. These differ from VPNs in that the proxies usually have limited functions compare to VPNs. | High |
| WEB | Web Proxies. These are web services which make web requests on a user's behalf. These differ from VPNs or Public Proxies in that they are simple web-based proxies rather than operating at the IP address and other ports level. | High |
Malicious Uses of Proxies and Prevention
Despite of using proxy servers for the purpose of personal privacy, it has been proven that anonymous proxy servers are often used to commit online frauds such as credit card fraud or spamming blogs and forums.
Therefore it is useful to have a software solution which allows users to identify anonymous servers and invisible or incorrect IP addresses for the purpose of personal protection.
IP2Proxy
IP2Proxy is a database subscription service from IP2Location.com which helps in IP geolocation and fraud prevention. IP2Proxy detects anonymous proxy by its IP address. The IP2Proxy database contains all proxy server’s IP addresses such as those used as VPN anonymizer, web proxies, open proxies and Tor exits.
IP2Proxy database is being updated every 24 hours. The service provider scans all IP addresses using a proprietary detection algorithm to identify anonymous proxies. Users can automate the daily download process to import the anonymous IP address list into server using download scripts.
Basic Structure of IP2Proxy in the CSV format
IP2Proxy IP-ProxyType-Country [PX2] database contains IP addresses which are used as data center ranges, VPN anonymizer, open proxies, web proxies and Tor exits in IPv4 range.
It contains 5 comma separated columns. Each row represents one IP address range with same proxy type. The first column "IP_FROM” represents the first IP number in network range. The second column "IP_TO” represents the last IP number in network range. The third column is the "PROXY_TYPE” which can be one of the five proxy types VPN, TOR, DCH, PUB and WEB. The forth column represents the ISO 3166 country code. The last column, which represents the country name also based on ISO 3166.
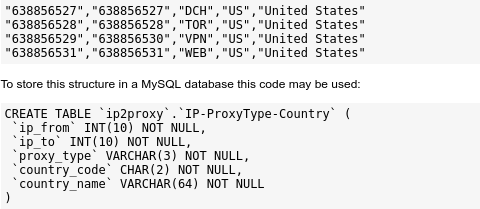
Below is a sample of the CSV file content:
"638856527","638856527","DCH","US","United States" "638856528","638856528","TOR","US","United States" "638856529","638856530","VPN","US","United States" "638856531","638856531","WEB","US","United States"
To store this structure in a MySQL database this code may be used:
CREATE TABLE `ip2proxy`.`IP-ProxyType-Country` ( `ip_from` INT(10) NOT NULL, `ip_to` INT(10) NOT NULL, `proxy_type` VARCHAR(3) NOT NULL, `country_code` CHAR(2) NOT NULL, `country_name` VARCHAR(64) NOT NULL )
The created table contains the following structure:
| Field | Type | Description |
|---|---|---|
| ip_from | int(10) | First IP address in netblock |
| ip_to | int(10) | Last IP address in netblock |
| proxy_type | varchar(3) | Type of proxy |
| country_code | char(2) | Two-character country code based on ISO 3166 |
| country_name | varchar(64) | Country name based on ISO 3166 |
How to Import the Database into MySQL
There are two ways to import the CSV data file into a MySQL database. The first one is using MySQL import tools like MySQL Workbench or phpMyAdmin. The second way to import the database in MySQL is by connecting to the MySQL server and import it by command line.
1. PHPMyAdmin
phpMyAdmin is an open-source tool for MySQL database operations using a Web interface. It is installed on nearly on every Web hosting server, and it can also be set locally. To import a CSV file to phpMyAdmin you will need a database and a table in phpMyAdmin.
After creating a database, the table can be created with this SQL code:
CREATE TABLE `ip2proxy` . `IP-ProxyType-Country` ( `ip_from` INT(10) NOT NULL , `ip_to` INT(10) NOT NULL ,`proxy_type` VARCHAR(3) NOT NULL , `country_code` CHAR(2) NOT NULL ,`country_name` VARCHAR(64) NOT NULL)
After selecting that table, there is an import option at the top of the interface. Selecting it, the import form will open. Under "format section” CSV is needed to be selected. A new form will appear, where the default values will be suitable for the file of IP2Location CSV database.
By selecting the file and clicking on Go or on Submit afterwards, the file will be uploaded to the database table, where it can then easily be searched, sorted and changed.
2. Command line
Using the shell command line is a way to communicate with MySQL server directly by connecting to it with the command "mysql -u UserName -p DatabaseName” which provides a shell like interface. For importing the CSV file, a database and a table will be needed again.
To create a table on a selected database, the code above is used. For shell interface some basic SQL is used so a simple knowledge of it is required.
To import the CSV file, it is needed to know the path of that file and the table name in the database, but also the database must be selected. Afterwards the column names of the table must be known. This is the SQL command used for the import process:
LOAD DATA LOCAL INFILE '/path/to/the/file/data.csv' INTO TABLE IP-ProxyType-Country FIELDS TERMINATED BY ',' ENCLOSED BY '"' LINES TERMINATED BY '\n' (ip_from, ip_to, proxy_type, country_code, country_name)
This code will load a local file /path/to/the/file/data.csv into the table IP-ProxyType-Country, where the fields in the data file are terminated by ',' as it is seen in the example above, enclosed by '"' and the rows terminated with a new line.
The columns from the CSV file must be ordered the same as the list of fields so they can match and everything is inserted in place.
How to Query the Database in MySQL
After importing the data into the database by a MySQL client like phpMyAdmin or directly with the command line, the query is very simple with a simple SELECT command. Here are some examples how to query the DB:
1. View all data
SELECT * FROM `ip-proxytype-country`
With this command all data in that table will be shown.
2. View all data from the United States
SELECT * FROM `ip-proxytype-country` WHERE `country_code` LIKE "US"
By using the country code, this SELECT command will filter the data and show only what has "US" in its field "country_code", which is the country code of USA.
3. View IP from and Type only
SELECT `ip_from`, `proxy_type` FROM `ip-proxytype-country`
This query will show only two selected fields in the result. It can also be filtered and narrowed like in the next example.
4. View IP from and IP to only for VPNs
SELECT `ip_from`, `ip_to` FROM `ip-proxytype-country` WHERE `proxy_type` LIKE 'VPN'
Finally this example is showing how to show the two IP's for the ones using VPN proxy type only.
IP2Proxy Web Service
In case the regular database import seems difficult, it is also possible to consider a hosted service.
The IP2Proxy Proxy Detection Web Service is a hosted service that allows instant detection of anonymous proxy, VPN and TOR exit nodes by IP address.
It is a REST API supporting JSON and XML responses. You can find more information about this service on the IP2Proxy Proxy Detection Web Service page.
Conclusion
If you are running Web sites or mobile applications that provide security sensitive services that can be abused by malicious users, it is important to block or restrict the access to users coming from VPN, TOR, proxies or data center ranges.
IP2Proxy Database or the IP2Proxy Web service can provide your application the necessary information to determine if your users are accessing your servers via known proxy servers.
If you liked this article, please share it. If you have questions about proxy servers and the IP2Proxy service, post a comment here.
You need to be a registered user or login to post a comment
1,616,872 PHP developers registered to the PHP Classes site.
Be One of Us!
Login Immediately with your account on:
Comments:
No comments were submitted yet.


